|
What is
the Matrix?
The Matrix
is the Information Galactic Highway. From the
smallest personal computer, to the Holonet, to the super
computers of the Imperial fleet.
But what
is it?
The MATRIX
could be described as a living computer entity. It
is an infinite world made up of billions of smaller
computer systems.
Slicers or
Hackers, or computer geeks. Whatever you call them,
be they hacking from home or be Corporate Sector Wage
Slaves, these are the ones who know how to 'surf' the
Matrix.
How the
Matrix appears to your PC's is up to you. Personally
I have each System be designed according to it's owner.
So Knight Industries system may well look like a Medieval
Castle, Reg's Speeder may appear as a Speeder Lot, while
Big Dick's home system could be.. well, anything.
When a
character enters the Matrix they can usually choose their
own form, though this may well depend on the system they
are accessing from.
Pocket
Computer (100 credits) - these have limited
access capabilities. Full Matrix access is not
possible as pocket computers don't have neural
connections.
Cyber-Deck
(500 credits - 2000 credits with implant connection) -
these are the tools of the true Slicer. Two kinds of
access is possible. A Neutal connector is placed on
the users temples, not requiring any implants, or via a
direct Cyber-jack implant. Either way transfers the
users consciousness into the Matrix.
Corporate
System (20,000+ credits) - As per a Cyber-Deck, though
usually much more powerful giving it's users extra
abilities and access to nearly unlimited software and
Cyberpunk Programs.
Layout
of the Matrix
CPU
(Central Processing Unit) - this is what controls the
system and is usually well guarded. Large
Corporations or Imperial systems will often have many
defenses. Once the CPU is accessed the Slicer can do
whatever he wishes to a system. The CPU can only be
Accessed by characters with Computer Engineer (A).
They will have to make an opposed roll vs. the CPU using
their Advanced (A) skill only.
| CPU
Access Modifiers |
|
| Dump
all users |
none |
| Delete
all Patrol Software |
+5 |
| Shut
down system |
+10 |
| Virus
infect the system |
+15 |
Security
Gate / Security Alert - in other words, 'What is your
password?' The Slicer must roll their Security skill
to by-pass Security Gates & Alerts. If the
Slicer rolls 3 less than the difficulty for a Security
Alert then an alarm will sound to the System
Administrator.
Data
Store - this is where the info is. It's the same
as a Windows directory or folder, though in the Matrix it
could appear as anything from a house to a blue ball.
Just because you can get the data though doesn't mean that
the file isn't passworded or in code.
Access
Terminal - whether from a pocket computer, Cyber-Deck,
or the on desk office terminal, this is where you access
from. Some access terminals can be remote access,
connecting the small system to the Computer Matrix.
Patrol /
Guardian / Sentinel - these are defense programs.
They can either sit in one location to protect a Data
Store or the CPU, or roam the system looking for
intruders. Without proper access codes these defense
programs will always attack, their aim being to dump
Slicers from the system.
A
Simple Computer System
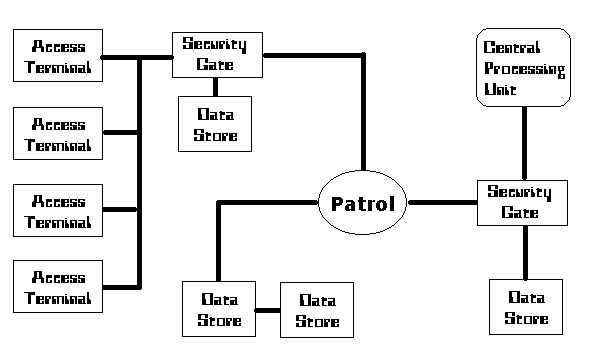
It works
like this: This system can only be accessed via one
of four Access Terminals. The user must first pass
the Security Gate (Moderate difficulty for a Slicer).
The user can either access the first Data Store
(Directory/folder) or continue to one of the next two Data
Stores. However, the System Administrator has
invested in a Patrol Program. Unauthorised users
would need to destroy the Patrol before proceeding.
There is then another Security Gate that needs to be
by-passed to gain access to the Data Store or the CPU.
This would be an Easy to Moderate system for a Slicer to
access.
You may not
want to always draw the system, especially for large
Corporations that have thousands of Access Terminals and
Data Stores. A Small area of the system could be
drawn, or describe it as it is viewed
eg. As
you exit the blue grass valley a castle only seen in fairy
stories, and on the Knight Industries corporate logo,
looms before you. As you approach you find that the
Draw-Bridge to the Castle is raised. To your right
is a computer post with four buttons requiring the correct
four digit sequence (This is a Security Gate: Moderate
Security is required). You now find yourself in
the courtyard with many smaller buildings in perfect order
(Data Stores). You hear the sound of hooves,
what do you do (PC "I hide" - roll dice).
Sorry, you failed to move quick enough. Before you
now is a magnificent white steed, it's rider dressed in
resplendent Knights armour wielding a menacing looking
Mace. (This is a Guardian - roll combat).
Data
Store Access Difficulties / System Costs / CPU Rating
| Type
of System |
Access
Difficulty |
System
Cost |
CPU |
| Personal
computer |
V.Easy-
Difficult |
100
cr - 1000 cr |
1D-2D |
| Small
Business |
Easy
- Moderate |
5,000
cr - 20,000 cr |
2D-3D |
| Large
Corporation |
Moderate
- Difficult |
100,000
cr - 1,000,000 cr |
4D-9D |
| Local
Government |
Difficult |
100,000
cr - 1,000,000 cr |
3D-5D |
| Imperial
Military |
Difficult
- Very Difficult |
100,000
cr + |
5D-10D |
Security
Security
Gate Moderate
500 cr
Security
Alert Difficult
1,000 cr
Computer
Guards
Computer
guards and intelligent programs that can either wait for
hackers or surf for the intruder.
| |
Search |
Security |
Computers |
Computers
(A) |
Cost |
| Patrol |
4D |
4D |
5D |
none |
5,000
cr |
| Guardian |
7D |
8D |
7D |
2D |
15,000
cr |
| Sentinel |
10D |
10D |
10D
- 15D |
3D -
5D |
30,000
cr |
Software
These
programs may be purchased, though restricted on some
worlds, to help access to computer systems.
Cyberpunk
Programs gives the Slicer a bonus onto their Attack or
Defense skills when in Combat. Slicer Programs give
other bonus's. Shadow software is used to hide from
Patrols or other system users, Skeleton Keys give a bonus
vs. Security Gates & alerts while Smart Bombs are
simply that, bombs that can be used against all patrols of
a type or against an individual (such as the system
Administrator who is trying to kick you out!)
|
Cyberpunk
programs
Attack
+1D
300 cr
+2D
500 cr
+3D
1000 cr
+4D
2000 cr
Defence
+1D
200 cr
+2D
400 cr
+3D
750 cr
+4D
1000 cr
These
are expended once the character disconnects from
the system. Being dumped therefore wastes the
program.
|
Slicer
Programs
Shadow Prog.
(Hide/Sneak)
+1D
200 cr
+2D
300 cr
+3D
500 cr
+4D
750 cr
Skeleton Key
(Security)
+1D
300 cr
+2D
500 cr
+3D
750 cr
+4D
1000 cr
Smart
Bomb
(dumps all guards of a type or used as a weapon
against a single target)
vs.
Patrol 500 cr
vs.
Guardian 1000 cr
vs.
Sentinel 2000 cr
vs.
All 10,000 cr
Damage
3D 200 cr.
Damage
5D 350 cr
Damage
7D 500 cr |
Each
program can be used only once. Using a ‘vs. All’ Smart
Bomb clears the system of all Computer Guards. However, it
would only take a moment for someone to reload them and
does not dump users.
Combat in
the MATRIX
It's got to
happen. It will happen, the first time you encounter
a Patrol. MATRIX combat is much like normal combat,
though no one really gets hurt, just dumped from the
system.
Skills
required:
Computers & Computer Eng (A)
MATRIX
Combat Skills
Computer Attack /
Defense Total - this
is the users Computers + Computer Eng (A)
You can
play Computer-wounds as per 2nd Edition rules, or
if you like my hit-point rules roll Computers to a Computer-Stamina
Point total.
Strength / Damage
- This is your characters Computers skill (do not add
Computers (A))
Computer
Combat
Each
character declares their actions (see below). Most
of the actions are for Advanced (A) skilled characters.
The Advanced (A) skill is added to the combat roll.
In order for the move to be successful the character must
move difficulty number with their Advanced dice only.
I therefore recommend using different coloured dice for
the Advanced. All dice are counted for the attac
total. Descriptions of moves are below.
Attack
Actions
Move Blaster
/ Melee / Brawl
Difficulty
none
Damage +0
Move Bolt
of Lightening
Difficulty
5
Damage +1D
Effect
Character form a bolt of lightening in their hand, firing
it at their opponent
Move Cyber-Tera
Kasi Kick Combo
Difficulty
10
Damage
+1D+2
Effect
Character levitates and delivers a multitude of kicks at
the target
Move Sphere
of Doom
Difficulty
15
Damage +2D
to all nearby targets
Effect
Creates a sphere of energy around character that explodes
outwards in all directions
Move Hack
/ Virus / Dump
Difficulty
Opponents Computer Eng (A) +5
Effect
Dumps opponent from the system
Move Unauthorised
Access / Alter opponents form
Difficulty
Opponents Computer Eng (A) +10
Effect
Either alter Opponents appearance or their Access so they
too are deemed as an Intruder.
Defense
Actions
Move Slow-time
dodge
Difficulty
5
Effect If
difficulty is made Roll an extra 1D for this Dodge or
Parry & count 6’s as in a Wild Die (ignore 1’s)
Move Lesser
Shield / Great Shield
Difficulty
10 / 15
Damage +1D
/ +2D Armour
Program
Terminates...
|
